Traefik an easy reverse Proxy
I was a long time user of Swag as reverse proxy, but since I discovered Traefik I started to use it more and more. And it became the core of my project YOC (Your Own Cloud).
For me the main advantage of Traefik, is all the configuration can be done directly on the docker-compose file and Traefik will automatically discover the services you want to reverse proxy.
Deploy Traefik
Traefik can be deployed with docker-compose, in this case, my domain is using cloudflare DNS, so I use the the Cloudflare API using my API Key to perform a DNS Challenge and get TLS Certificates with Let's Encrypt.
If you don't setup any DNS challenge, Traefik will create a self signed certificate.
---
version: "3"
services:
traefik:
container_name: traefik
image: traefik:v2.10
command:
- --api.insecure=true
- --providers.docker
- --log.level=DEBUG
- --entryPoints.web-secure.address=:443
- --certificatesresolvers.letsencrypt.acme.dnschallenge=true
- --certificatesresolvers.letsencrypt.acme.dnschallenge.provider=cloudflare
- --certificatesresolvers.letsencrypt.acme.email=YOUR_EMAIL_ADDRESS
- --certificatesresolvers.letsencrypt.acme.storage=/letsencrypt/acme.json
- --entrypoints.web-secure.http.tls.domains[0].main=YOUR_DOMAIN_NAME
environment:
- CF_DNS_API_TOKEN=YOUR_CLOUDFLARE_API_KEY
ports:
- 443:443
- 8080:8080
volumes:
- /var/run/docker.sock:/var/run/docker.sock
- /PATH/LOCAL/STORAGE/traefik/letsencrypt:/letsencrypt
restart: alwaysMake sure to replace /PATH/LOCAL/STORAGE with your local data folder.
If you want to use Cloudflare (or other) to get TLS Certificate for your domain, make sure to replace:
YOUR_EMAIL_ADDRESSwith a valid email address for Let's EncryptYOUR_DOMAIN_NAMEwith your own domain nameYOUR_CLOUDFLARE_API_KEYwith your Cloudflare API Key..
If you want to use a self signed certificate with Traefik, you can leave YOUR_EMAIL_ADDRESS and YOUR_CLOUDFLARE_API_KEY empty so Traefik will generate automatically a self signed certificate, and set --certificatesresolvers.letsencrypt.acme.dnschallenge to false.
Running Traefik with Docker Compose
Now that we have our Docker Compose file ready, let's proceed with running Traefik:
Run the following command to start the Traefik service:
docker compose up -dOnce every container started you can access your Traefik instance with http://your_server_ip:8080
You will access the Traefik Dashboard
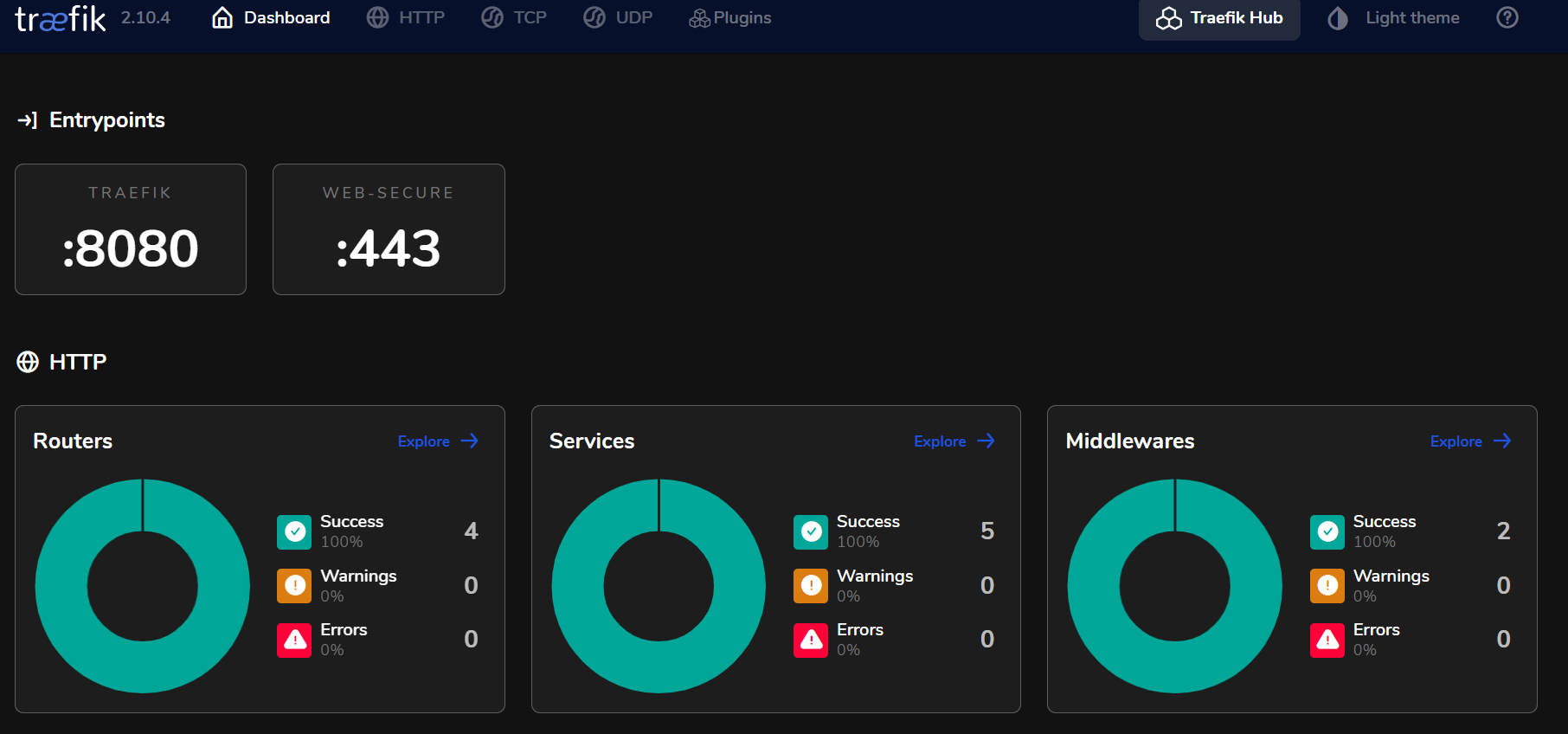
Adding Vaultwarden as a service.
Ok so now we have Traefik and up and running we need to be able to use it as reverse proxy.
In this example we are going to use Vaultwarden as a service we want to access using Traefik.
Let's start from our previous docker file and let's add the Vaultwarden container.
my.domain---
version: "3"
services:
traefik:
container_name: traefik
image: traefik:v2.10
command:
- --api.insecure=true
- --providers.docker
- --log.level=DEBUG
- --entryPoints.web-secure.address=:443
- --certificatesresolvers.letsencrypt.acme.dnschallenge=false
- --certificatesresolvers.letsencrypt.acme.dnschallenge.provider=
- --certificatesresolvers.letsencrypt.acme.email=
- --certificatesresolvers.letsencrypt.acme.storage=/letsencrypt/acme.json
- --entrypoints.web-secure.http.tls.domains[0].main=my.domain
environment:
- CF_DNS_API_TOKEN=
ports:
- 443:443
- 8080:8080
volumes:
- /var/run/docker.sock:/var/run/docker.sock
- /PATH/LOCAL/STORAGE/containers/traefik/letsencrypt:/letsencrypt
restart: always
vaultwarden:
image: vaultwarden/server:latest
container_name: vaultwarden
environment:
- SIGNUPS_ALLOWED=true
- DOMAIN=https://vaultwarden.my.domain
volumes:
- /PATH/LOCAL/STORAGE/containers/vaultwarden:/data
ports:
- 80
restart: always
labels:
- traefik.http.routers.vaultwarden.rule=Host(`vaultwarden.my.domain`)
- traefik.http.routers.vaultwarden.entrypoints=web-secure
- traefik.http.routers.vaultwarden.tls=true
- traefik.http.routers.vaultwarden.tls.certresolver=letsencryptThis is the basic Vaultwarden docker compose configuration, but to make it work with Traefik we added labels:
labels:
- traefik.http.routers.vaultwarden.rule=Host(`vaultwarden.my.domain`)
- traefik.http.routers.vaultwarden.entrypoints=web-secure
- traefik.http.routers.vaultwarden.tls=true
- traefik.http.routers.vaultwarden.tls.certresolver=letsencryptThose labels allow us to tell Traefik we want Vaultwarden to be accessible from vaultwarden.my.domain, using the entrypoint web-secure and using TLS.
Traefik will automatically see Vaultwarden is listening on the port 80 and create reverse proxy rules based on it. You dont' have to restart the Traefik container when adding services.
Now we restart everything with docker compose up -d.
After a few seconds, you can access https://vaultwarden.my.domain
vaultwarden.my.domain, I added *.my.domain as a DNS Rewrite in my AdGuard Home server. You can also modify your hosts.conf file.
Conclusion
Traefik is really fast and easy to use, but compared to Swag some useful tools are missing, for example Swag natively support Authelia for Authentication / MFA and SSO and also natively support Fail2ban. Traefik don't.

